Key Takeaways:
- Network Access Control (NAC) is pivotal for robust cybersecurity and protecting information assets.
- Compliance with regulatory standards is crucial to implementing a strong NAC system.
- Best practices in NAC implementation can significantly elevate an organization’s security posture.
- The rise of mobile and IoT devices necessitates an adaptive and thorough NAC strategy.
- Future trends in NAC promise enhanced security through machine learning and AI integration.
Table of Contents:
- Introduction to Network Access Control
- Essential Components of Network Access Control Systems
- Protecting Assets With Network Access Control
- NAC’s Role in Regulatory Compliance
- The Impact of Mobile and IoT on NAC
- Implementing Network Access Control: Best Practices
Introduction to Network Access Control
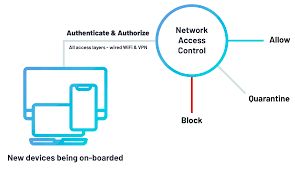
Establishing a multifaceted defense system is paramount for businesses in the ever-evolving landscape of digital threats. An integral component of such a system is Network Access Control (NAC), which ensures that individuals and devices are authenticated before granting them the appropriate level of access. This security measure is a gatekeeper against unauthorized entry, protecting the network by monitoring who can connect and what resources they can use. When effectively deployed, network access control offers a dynamic and adaptable defense mechanism that can scale with the growth and complexities of a business’s technological ecosystem.
The development of NAC has been significant, with the solutions becoming more advanced to meet the demands of modern network environments that extend beyond physical office spaces. Companies now face the challenge of securing remote workforces, cloud infrastructures, and various personal and corporate devices. Thus, NAC is crucial for securing traditional network perimeters and providing secure access across distributed networks, ensuring that security policies are consistently enforced, whether a user is on-site or connecting remotely.
Essential Components of Network Access Control Systems
Effective Network Access Control systems are built upon several key components that harmonize to secure network access points. These components include authentication, authorization, and accounting (AAA) protocols, ensuring that all users and devices are thoroughly vetted before accessing network resources. A powerful NAC solution also employs a sophisticated policy engine that can manage these AAA protocols in real-time, adjusting access permissions based on user role, device compliance, location, and even access time.
On the forefront of network security, authentication is the first barrier, determining whether users and devices can establish a foothold within the network. Typically, this involves validating credentials against a directory service such as Active Directory. However, as cyber threats become more sophisticated, multi-factor authentication (MFA) mechanisms that combine passwords with biometrics or one-time codes have become standard for stronger security assurance. Authorization then builds upon authentication, enabling granular control over what resources users can access and the actions they may perform.
Protecting Assets With Network Access Control
NAC is vital in protecting business assets by controlling and monitoring access to a network’s resources. This prevents unauthorized access by external actors and manages the internal use of resources, limiting the exposure of sensitive data to users and devices that do not need it for their day-to-day duties. In essence, NAC serves as both a gatekeeper and a steward of network assets, reducing the attack surface that can be exploited by cyber threats and playing a key role in both preemptive security strategies and reactive incident responses.
Furthermore, the versatility of NAC systems comes from their ability to integrate with other security platforms and services. This comprehensive approach means that NAC does not operate in isolation but rather contributes to an overarching security framework that includes firewalls, intrusion prevention systems (IPS), anti-malware tools, and data loss prevention (DLP) solutions. Such integration enables a more cohesive and proactive security posture, where threats can be quickly identified and mitigated, minimizing potential damage to the organization’s operations and reputation.
NAC’s Role in Regulatory Compliance
Regulatory compliance is a complex yet unavoidable aspect of modern business operations. Data protection laws and industry-specific regulations impose stringent requirements on how organizations must secure and handle sensitive information. NAC is instrumental in meeting these demands by providing the necessary controls to manage user access to protected data.
The Impact of Mobile and IoT on NAC
The proliferation of mobile and IoT devices has expanded the number of endpoints that must be secured within a network. This challenges traditional NAC systems, as these devices often need to be accountable to the same security standards as desktops and servers. Modern NAC solutions address this by implementing dynamic policy engines that can adapt to the security profile of each specific type of device. By extending security policies to mobile and IoT devices, NAC systems ensure they do not become vectors for security breaches.
In a landscape where a single unsecured device can be the entry point for a major potential breach, an organization must have a NAC solution capable of managing the complexity and variety of today’s mobile and IoT devices. NAC systems must be able to assess the compliance status of devices in real-time, enforce appropriate access controls, and even isolate or remediate non-compliant devices that may pose a risk to the network.
Implementing Network Access Control: Best Practices
Introducing a NAC system into an enterprise must be handled carefully and carefully. Given the intricacies of network environments, only implementing a NAC system with proper planning can lead to disruptions and potential security gaps. Organizations are advised first to conduct a comprehensive network assessment. This diagnostic step is important for identifying the existing network infrastructure, understanding the data flow, and recognizing the organization’s specific security needs.



